After the Hack
A $30M hack in late December, for victims, it was not a happy holiday. It was… grim. The story of the Grim Finance hack And the team's attempts to make things right
In December 2021, Grim Finance, a yield aggregator operating on the Fantom Opera blockchain, suffered a significant exploit resulting in the loss of approximately $30 million in user funds.
The attacker took advantage of a reentrancy vulnerability in one of Grim's vault contracts. Despite Grim labeling the attack as “advanced,” this was a garden-variety exploit that could have been avoided with a more thorough security review.
Grim paused all vaults, notified exchanges, and reached out to law enforcement, security experts, and the hacker to try to recover funds. This was the good part of their response and belongs in every project's incident response plan.
They probably could've done without the frantic, all-caps EVERYTHING IS SAFE announcement though.

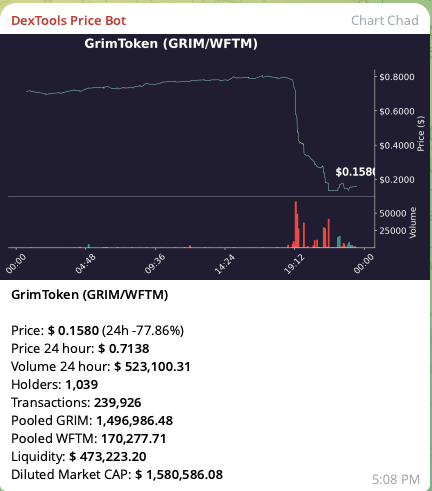
Despite the pause, GrimToken plummeted ~80% amidst the chaos following the hack. Plunging token price is one of the recurring elements of the post-hack death spiral. Best chance to avoid is having an incident response plan in place before a hack occurs.
Grim quickly announced plans to “create and deliver an effective compensation plan.” But users were… skeptical.
Again, if there were a plan set up in advance, might it have inspired more confidence?

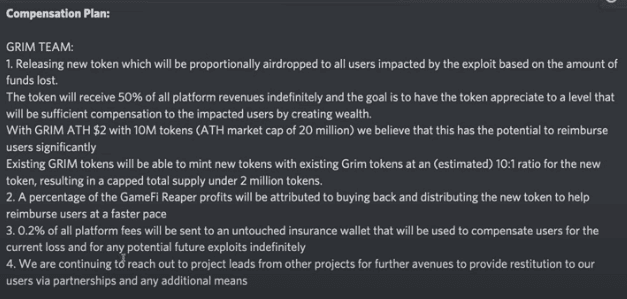
Grim did announce their compensation plan and if it wasn't entirely “effective” it was generous, with 50% of future revenue going to holders of the compensation token.
The reaction was mixed, with some users being appreciative and optimistic and others skeptical and impatient.
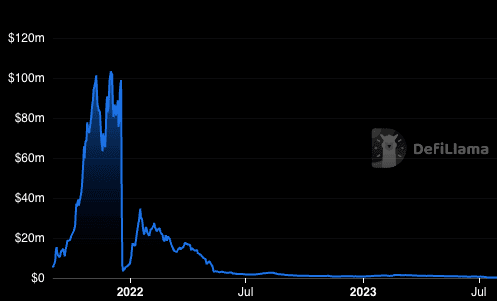
Admirably, the Grim team went back to work, releasing a v2 and lots of new vaults. According to DefiLlama, they bounced back to a peak of ~$35m TVL in Jan 2022. But they could never regain the pre-hack momentum and flatlined as 2022 wore on.
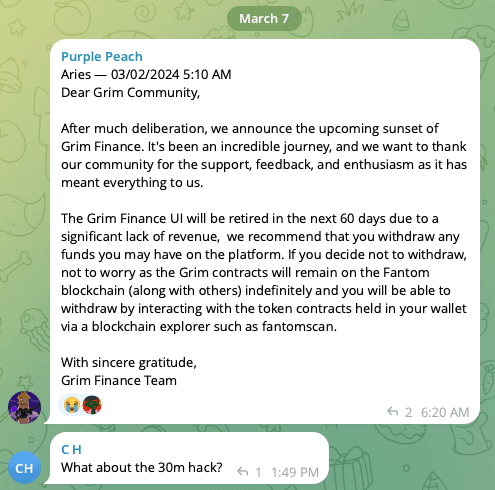
In early 2024, Grim finally shut down the protocol. Users were left still asking “wen compensation?”
Despite what appears to be genuine efforts to do right by the developers, Grim falls into a pretty common archetype of what not to do:
- have no plan for recourse in the event of a hack
- get hacked, losing the community's trust and much of the protocol's value
- announce a well-meaning plan to compensate users with future profits
- shut down
Grim's biggest mistake was missing the exploit in their security review process. Their second biggest mistake was not having a plan in place in case they did get hacked.
It didn't have to be like this. Avoid this ghastly future and codify your incident response plan now.